The new economy is digital. It’s in the trillions, so increasing digitization of the world has led to an increased risk that some parts of the ecosystem will be compromised.
It’s no surprise then, that a ton of cybersecurity firms have emerged and attempted to dominate the landscape of ensuring and maintaining data privacy. However, each solution so far has brought with itself increasing endogenous risk to its own line of business.
Plurilock offers a cybersecurity solution that’s rooted in behavioral biometrics. Here’s what that means: their solution to approaching the problem of cybersecurity is rooted in both – the data, the systems-level framework that is used to create secure ecosystems, and the human action that complements it. Before we dive into their technology, let’s take a look at existing ways in which cybersecurity infrastructures work:
Current Approaches
Traditionally, security protocols mostly end up over-relying on a singular framework to enhance security.
For instance, if you’re an email user, passwords are the sole gatekeeper of privacy, and security here is enhanced primarily by choosing more secure passwords. It’s the reason why most websites ask for special characters, capitalized letters, and strings of numbers to ensure that passwords are “unhackable” – to the degree that they are unpredictable.
On the other end of the spectrum, you have purely biometric authentication systems that rely on a specific set of data. TouchID on the iPhone is a popular example, where security is afforded to the platform via an individual’s unique fingerprint. Across industries, this translates to iris scanners, or a combination of biometric and technology solutions to enhance security.
Even in this instance, what happens is that an individual’s biometric inputs are converted to a layer of data via sensors and technology, and that data is then used to authenticate interactions.
The central problem with either of these approaches is that it carries an inherent risk of over-relying on a single factor, or quality of data inputs to enhance security.
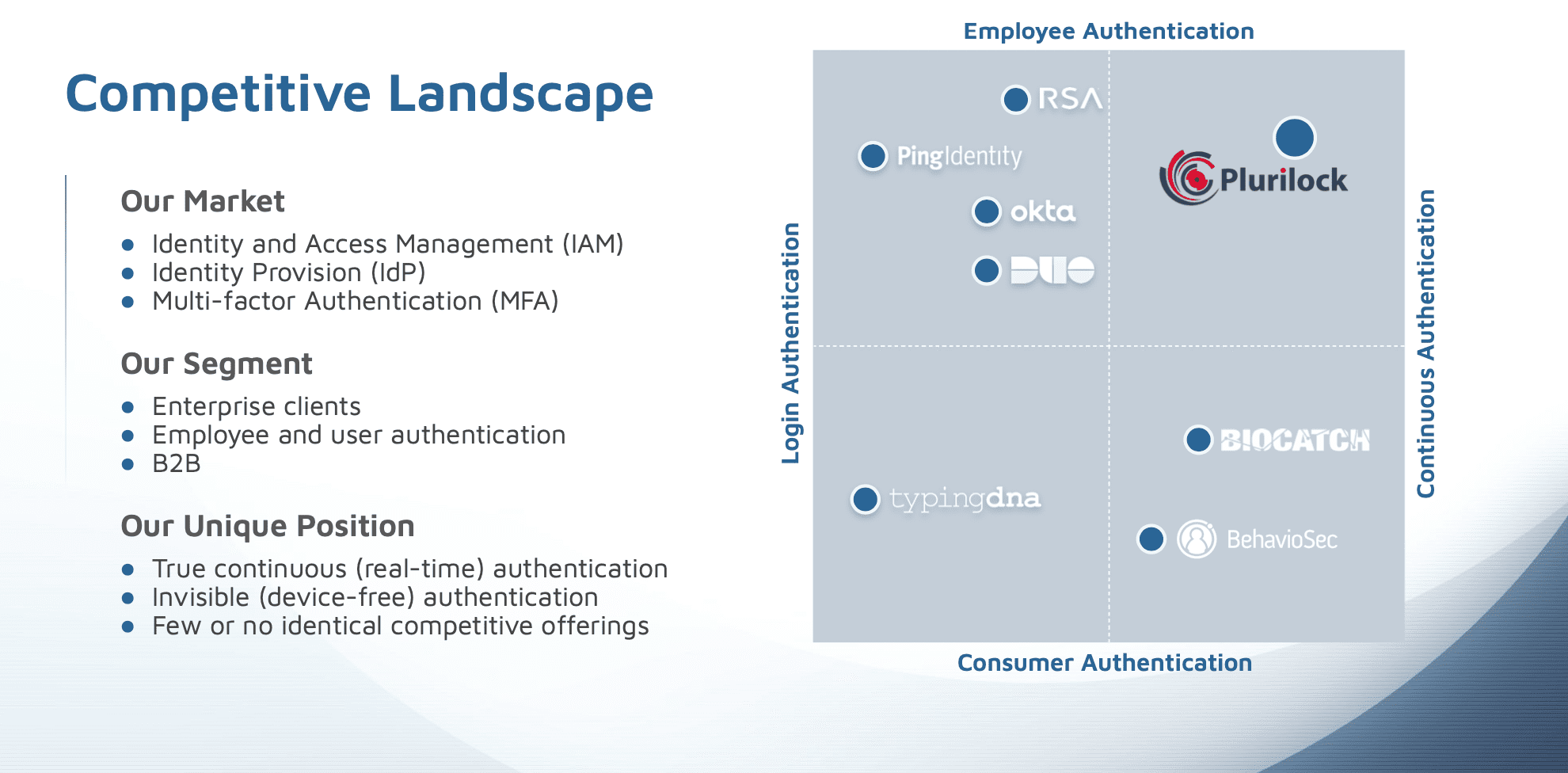
Plurilock’s Solution
Plurilock’s technology mitigates that risk by offering a solution that incorporates unique patterns of behavior along with biometric inputs. Together, their offering affords a solution that is complementary to human-computer interaction.
Simply put, their cybersecurity solution incorporates micro-patterns that are emergent in user behavior. It’s not just your password, it’s also the speed and accuracy with which you enter your password. It’s not just a fingerprint scan, but also the degree of pressure with which you press on a sensor.
In effect, their solution adds a complementary layer of authentication that is unique, and user-specific. So EVEN IF you posit that someone will get access to your password, they won’t be able to get access to your files because the way someone else would input the same data on a computer, will be categorically different than the way you enter data.
Integrating these micro-level patterns of user behavior over a layer of existing security protocols achieves two key objectives.
First, it means that their algorithm is continuously evolving and adapting to user patterns and use cases. This translates to greater security as authentication is never dependent on a singular factor or a data set that is susceptible to theft or hacking.
Second, it means that the complementary layer of security afforded means reduced expenditure costs to enhance security protocols. So existing firms do not need to add another layer of authentication with code-generators for each login attempt or another biometric scanner to scan your iris. Any and all existing solutions can be made more secure by adding Plurilock’s technologies. Most importantly, existing solutions already collect these data points that can be made more secure via Plurilock technology.
The Business
Now that we’ve understood the solution, let’s dive into the business. Because Plurilock’s solution is complementary to existing infrastructures, security can be enhanced at a much cheaper marginal cost.
Currently, the company has two key lines of product: ADAPT and DEFEND.
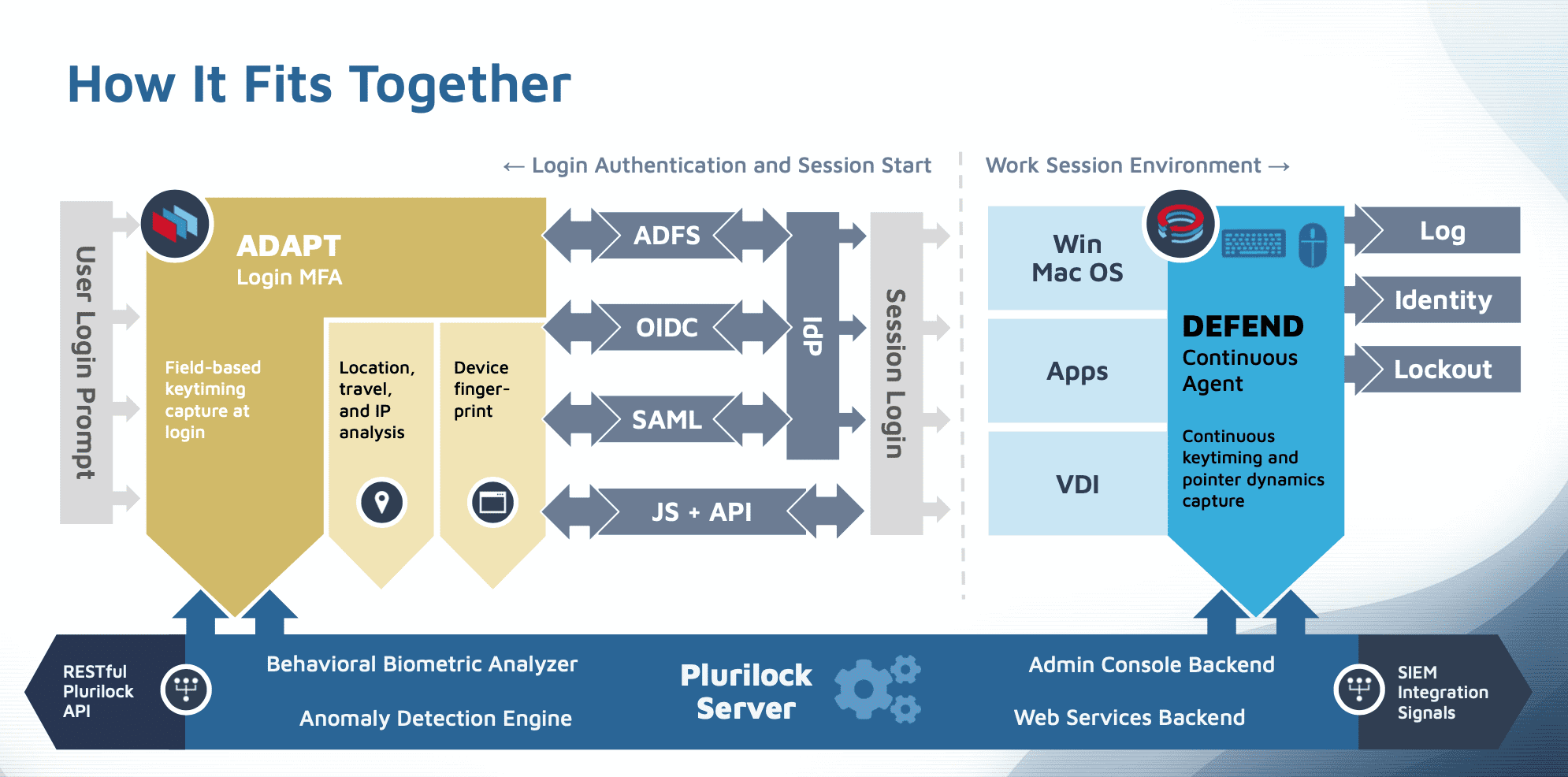
The central difference between the two is that the former caters to authenticating user-level workflows (think: entering your password to log on to Gmail), while the latter provides continuous authentication for endpoints and workstations (think: how you behave and work once you’re inside Gmail).
This means that the security isn’t merely afforded when one logs on, but is ensured while users are working within a specific ecosystem.
Imagine a financial institution that requires users to log-on to their cloud-based platform for day-to-day work. Plurilock’s solution will first apply security checks when one logs on and will ensure that the system is secure while one is working.
So even if you assume that someone, somehow, gets access to login credentials to engage in phishing activities, continuous authentication running in the background will ensure that the breacher doesn’t stay within the system.
As a software business, their offering is priced on a SaaS-based model, with $3/user/month for ADAPT, and $9/user/month for DEFEND. For enterprise-level customers, discounts are available, but are also locked to three-year contracts, ensuring 1) recurring cash flow, and 2) increased accountability for Plurilock.
The market for Plurilock’s offering encompasses anyone and everyone in a business that needs enhanced cybersecurity. From banks to corporations to the military, cybersecurity is a key factor that can make or break success.
In fact, the lack of secure cybersecurity protocols can cost businesses, especially financial institutions, who will be unable to pass regulatory audits. These types of institutions are increasingly in need of enhanced security protocols at the individual and at the enterprise level.
Because Plurilock’s solution is software-based, its implementation doesn’t increase user friction or incur product cost of a code-generator, etc, which requires training and/or navigation. By including the unique, micro-level patterns of behavior in human-computer interaction, the firm offers a solution that increases security, decreases cost, and decreases user friction across all levels of operation.
Above all, the best part about the technology is that it is scalable. A small and talented team has been able to develop a product whose use cases span industry verticals. I’m excited to see the investment opportunity Plurilock Security Solutions Inc. offers to retail investors looking to back sustainable technologies that protect and safeguard the way we operate in our digitizing world.


Leave a Reply