Even in a corporate environment where everyone is working out of the same office, network security is a pain in the ass. Logins and password changes and IP addresses and VPNs and lockouts and long calls to annoyed support staff all make for an awkward process of establishing who exactly is sitting at the keyboard. And when you’re working from home, as many of us now are, the situation becomes infinitely worse.
Passwords are notoriously unsafe and easy for machines to crack.

Even something as exotic as a retina scan doesn’t help as much as you think – once a login scan has been made, the system is basically open if someone else sits down at the keyboard. A fingerprint scan likewise – and let’s not even think about the possibility of someone taking one of your fingers with them to get access to something they want.
Mostly though, the big risk at the network level is someone logging in, then going away to get a coffee and leaving their machine unmanned. Or someone giving up their password accidentally in a phishing scam. Or someone accessing the system from an insecure network. Or someone leaving their laptop in the back of a cab after a night of Jagerbombs.
To combat this, companies use a patchwork of competing security tools, all of which get in the way of people actually doing business as often as they keep things secure.
Over 80% of computer network security breaches come from stolen logins. To combat this, we’re told we should have multi factor authentification – a code sent to your phone that needs to be typed into the computer, as an example. But if a hacker has my phone, or has told the phone company to switch my sim card for his, he’s in.
You could add more steps to the authentification – let’s say I can only connect from a given location – but that means I cant connect from a cafe during my lunch, or from my home office during Covid, or my car on the side of the road during a conference call.
Even passwords themselves are an annoyance – these days they’re 8-10 characters, with non-numerics and caps and a fucking umlaut here and there, and god forbid there’s a Captcha system that wants me to click in every picture with a traffic light in it.

I don’t mind telling you, I hate computer security. Yeah, I’ll change my password when told, but I’m like anyone else – I’m going to do the minimum I have to, and only then begrudgingly. That makes me, if I’m part of a large organization, a particularly large security hazard. I’m also in the majority on that.
So what if the entire system was rethought to be constantly watching the user, to see where they are, what they’re doing, and analyzing their typing pattern? Not looking at their work but at HOW they work, to notice if those patterns are unusual and only then prompt for ID?
What if your password wasn’t a word, but the way you typed words?
‘All day authentification’; That’s the system Plurilock employs as a way of helping companies get network security processes out of the way while actively engaging in them more often.
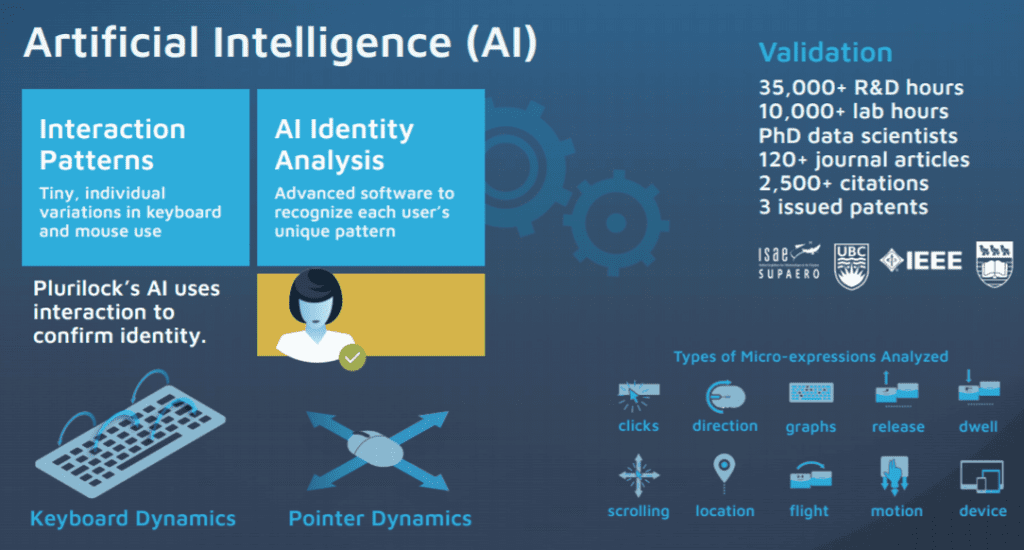
The way you use your mouse, the things you click on, the way you scroll, how you switch tabs, the devices you use – these are all ways to identify user patterns throughout the day. If you suddenly typed lefthanded, or even positioned your hands differently so there was a slightly longer pause between your T and H, the system would catch that and start looking at you askance. If your mouse moved a little faster than usual, that’d be another flag. If you open a dozen tabs and leave them open, that’d be more useful info. And hey, you’re logged in from Gdansk instead of Medicine Hat, and you DON’T have PornHub open in the background in the late afternoon.. okay, WHO EXACTLY ARE YOU?
Here’s more:
I like a Software as a Service (SaaS) deal that locks in client in for multi-years, and Plurilock does that. At between $3 and $9 per user, per month, the system is not so expensive it’s a hard sell, and sticky enough that once you’re using it, it’s hard to stop. For government organizations and financial services firms, this sort of thing is a no-brainer.
But starting out trying to sell to mid-level majors is hard going, so Plurilock is working on a series of transactions to acquire existing security businesses that both compliment Plurilock’s existing offerings, but also come with market share, using stock as acquisition capital.
The early action on Plurilock since it’s landed on the public market has been mixed. Good days and down days. That’s mostly because the company is too new to have stacked up a significant amount of news just yet, and its first public quarterly financial statements showed a small loss.
But the company has raised enough cash to see it through a nice amount of growth period, the website has exactly the amount of detailed information you’d be hoping for to show this is a real company and not a theory with a ticker symbol, the executive suite includes folks with significant pedigree, and the demand for what they’re selling is, if my own consideration for it in our own business is any indicator, strong.
Our Gaalen Engen had a chat with Plurilock CEO Ian Paterson to get more detail.
Behavioural biometrics is an emerging field, and this team originally stemmed from work done in the University of Victoria, so when I look at the potential for Plurilock, I see a tool that could become as widespread as Captcha is, with a potential for revenue that could touch every large corporation in the world.
For investors looking for a quick flip, this ain’t it. Rather, Plurilock will likely be a long slow builder, chipping away one customer at a time, until someone much larger sees the potential for it when scaled.
At just a $12 million market cap right now, I’m in, and will be in for some time.
— Chris Parry
FULL DISCLOSURE: Plurilock is an Equity.Guru marketing client.


Leave a Reply